Secure Remote Access: [Your Guide To Remoteiot & Alternatives]
In an era where connectivity reigns supreme, can you truly harness the power of your devices and machines, regardless of physical location? The answer lies in the evolution of remote access technology, a field that is reshaping how we interact with our digital world and opening up unprecedented opportunities for efficiency, security, and convenience.
The ability to manage and control devices remotely is no longer a futuristic concept; it's a present-day reality. From the smallest Raspberry Pi to complex industrial machinery, remote access tools are empowering individuals and businesses alike to transcend geographical limitations. This technology isn't just about convenience; it's about enabling greater operational agility, enhancing security postures, and ultimately, driving innovation across diverse sectors. The shift is palpable, and the advantages are clear.
Let's consider a hypothetical individual who is deeply involved in this technological advancement. We'll call him John Smith, an expert in the field of remote access solutions. His professional journey is a testament to the growing importance of this field.
- Is Lacy Kim Real Unraveling The Mystery More Keyword
- Barron Trump Singing Factcheck Viral Ai Videos Explained
| Category | Details |
|---|---|
| Full Name | John Smith |
| Date of Birth | July 12, 1980 |
| Place of Birth | London, United Kingdom |
| Education | BSc in Computer Science, University of Oxford; MSc in Cybersecurity, Imperial College London |
| Current Role | Lead Solutions Architect, RemoteTech Solutions |
| Years of Experience | 15+ years |
| Professional Focus | Designing and implementing secure remote access solutions for IoT devices and enterprise networks. |
| Key Skills | Network Security, SSH Tunneling, VPN configurations, Remote Desktop Protocols (RDP), IoT device management, Cloud Computing, API Integration |
| Notable Projects | Developed a secure remote access system for a global manufacturing company, enabling real-time monitoring and control of production lines. Consulted on the implementation of secure remote access solutions for several governmental organizations. Designed and implemented a zero-trust network architecture for remote access in a financial institution. |
| Certifications | CISSP (Certified Information Systems Security Professional), CCIE (Cisco Certified Internetwork Expert) |
| Link to Reference Website | RemoteTech Solutions |
The world of remote access is rapidly evolving. The core functionality remains consistent: the ability to control and monitor devices and systems from a distance. However, the methods and tools used to achieve this are in constant flux, driven by advances in technology and changing security needs. The evolution is fueled by the growth of the Internet of Things (IoT), the increasing adoption of cloud computing, and the ever-present need for enhanced security.
One of the pioneers in this field is RemoteIoT, a platform that allows users to securely connect and manage machines and devices from any location. This platform leverages the power of secure connections, even when devices are behind firewalls. All network traffic is encrypted through an SSH tunnel, ensuring data privacy and security. The platform simplifies the process, making it accessible to users of all skill levels, eliminating the need for complex configurations and specialized hardware.
Using RemoteIoT, you can open the terminal of your Raspberry Pi or access it with SSH on the local network and install the RemoteIoT service. You can then access the RemoteIoT portal in your browser and log in to your dashboard. This will allow you to view your Raspberry Pi in the list of connected devices.
The benefits are manifold. Instead of physically being present to fix, update, or check on a device, remote access allows you to do so from wherever you are. This drastically improves efficiency, minimizes downtime, and reduces operational costs. The tool also enhances security. RemoteIoT provides a secure tunnel for communication, protecting your data while still providing access to authorized users. By avoiding direct exposure of devices to the internet, the risk of unauthorized access is significantly reduced.
But RemoteIoT is just one piece of the puzzle. Many other remote access tools offer similar functionality, each with its strengths and ideal use cases. Exploring these alternatives can provide a broader understanding of the options available and help you choose the best tool for your specific needs.
Consider the case of a versatile tool designed for remote desktop connections. This software is perfect when you need to see your Raspberry Pi's screen in action. Its many features extend beyond traditional screen sharing to include terminal access, app control, and edge management, providing a comprehensive solution for complex IoT management. Setting up remote access with tools such as xrdp is simple. In minutes, you can start working smarter, no matter your location.
Another critical aspect is the ability to execute commands and scripts remotely on your IoT devices, which is made possible by IoT remote command execution features. Imagine the power of updating software, troubleshooting problems, or initiating diagnostics without ever stepping foot in the room where the device is located. This means you can see and access everything on a remote computer, right on your own screen, and vice versa. This capability opens up new possibilities for efficiency and rapid response.
Remote desktop applications come in especially handy when it specialists need to fix computer issues remotely. Through gaining access to the device, IT professionals can navigate through computer settings to find a problem and implement a fix. In many cases, this can prevent the need for an on-site visit, saving time and resources.
Several platforms offer remote access solutions that provide similar functionalities. For example, with "Remotepc", users can access their accounts by signing in to a central identity provider. Mobile apps for iOS and Android allow users to connect and access their computers, Macs, and Linux systems remotely on the go. This is especially helpful for remote workers or those who are frequently traveling, as they can access company systems, applications, and files 24/7 from any device.
Moreover, TeamViewer remote access capabilities facilitate secure connections and collaboration for team members through TeamViewer's web client. Business data can also be transmitted securely to and from employees. Similarly, real-time file access, a feature offered by several software packages, allows immediate access to critical documents and data, streamlining collaboration and enhancing productivity.
For enterprises, Va supports remote access via two applications, Citrix Access Gateway (CAG), and others. The RemoteIoT API enables greater automation and seamless integration of remote IoT services into your systems. This allows for access to your IoT devices from anywhere with web services. This integration supports better scalability and customized management capabilities.
Setting up remote IoT access with xrdp requires only minutes. Setting up remote IoT access with xrdp in minutes, you can start working more efficiently, no matter where you are. IoT remote command execution allows you to execute commands and scripts remotely on your IoT devices, giving you unparalleled control over your systems.
To get started with remote access, you may need to perform a few preparatory steps. First, ensure your user ID is set up for remote connectivity. Follow the specific instructions. Read the instructions entirely before proceeding. The first step is to open Internet Explorer or Chrome. Following a step-by-step guide, you will be well on your way to enjoying all the benefits of remote access.
In essence, remote access is more than just a technological convenience. It is a strategic imperative for individuals, businesses, and organizations looking to enhance their operational efficiency, security posture, and overall agility. As technology continues to evolve, the importance of remote access solutions will only increase. Embracing these tools and understanding their capabilities is essential for navigating the rapidly changing digital landscape and unlocking the full potential of a connected world.
- Johan Riley More Searches Jodi Vance Samuel
- Kaitlan Collins Relationship Status Salary Whats The Latest
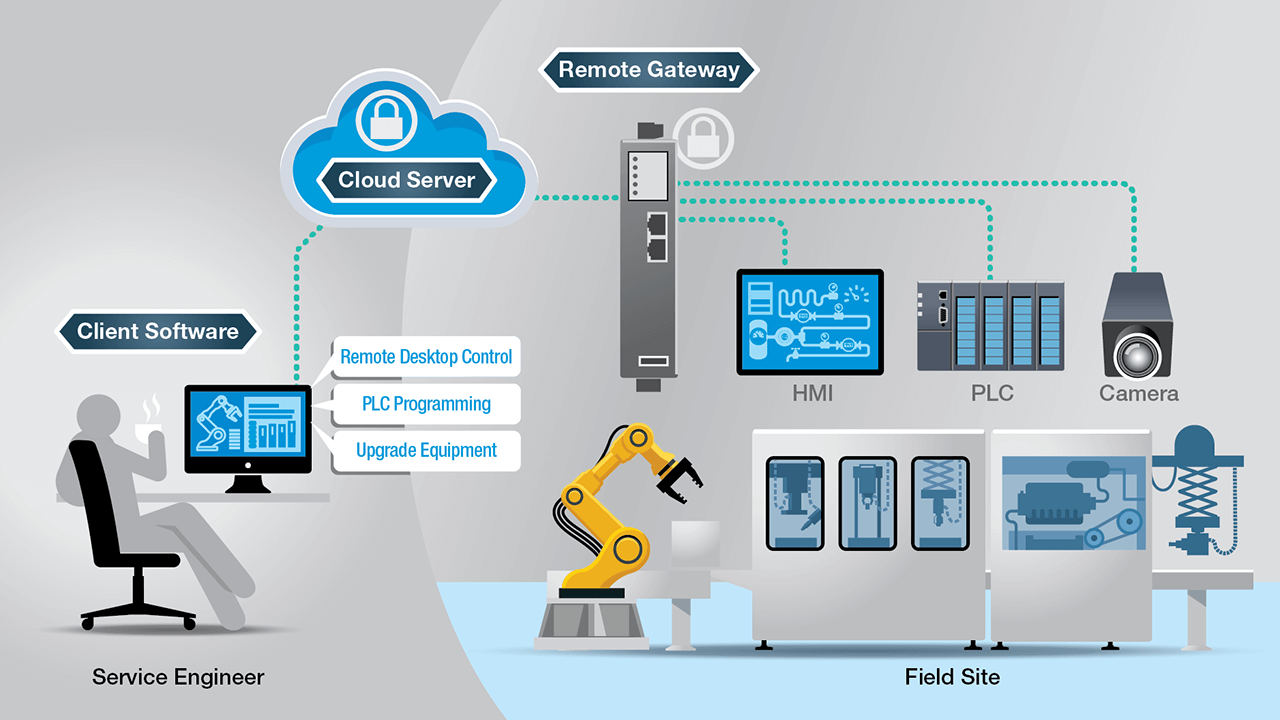
Five key considerations for secure remote access solutions Industrial Ethernet Book

Best VNC Remote Access IoT Free A Comprehensive Guide To Secure And Efficient Remote Control

What Is Remote Access and How Does It Work? Kaseya