Remote IoT Access: Your Guide To Secure Device Management & Beyond
Are you struggling to manage your Internet of Things (IoT) devices scattered across remote locations? The ability to remotely monitor, control, and maintain your IoT infrastructure is no longer a luxury, but a necessity for operational efficiency and security in today's interconnected world.
In today's rapidly evolving technological landscape, the ubiquity of IoT devices is undeniable. From smart home appliances to industrial sensors, these interconnected devices are transforming the way we live and work. However, with this widespread adoption comes the challenge of effectively managing these devices, especially when they are deployed in remote locations far from a company's IT support team. This is where remote IoT device management becomes crucial.
The scenario of devices operating independently in remote areas presents unique hurdles. Troubleshooting becomes difficult, physical access is limited, and security threats loom large. Addressing these challenges requires a comprehensive approach, encompassing secure communication, robust monitoring tools, and efficient management strategies. Luckily, several solutions exist to address these challenges, ensuring seamless operation and optimal performance of your IoT ecosystem.
- Remote Iot Management Secure Setup Solutions You Need
- Lori Pettys Relationships Love Life Career Revealed
Remote IoT device management is not just about convenience; it's about ensuring the longevity, security, and efficiency of your IoT deployments. It allows businesses to maintain operational control, reduce downtime, and minimize the need for costly on-site visits.
| Aspect | Details |
| Definition | The practice of managing and maintaining Internet of Things (IoT) devices from a remote location. This includes monitoring, troubleshooting, updating, and controlling devices that are often deployed in geographically dispersed areas. |
| Key Components |
|
| Benefits |
|
| Common Tools and Technologies |
|
| Use Cases |
|
| Security Considerations |
|
| Future Trends |
|
| References | Example IoT Management Website |
One of the simplest approaches involves using SSH with a VPN or proxy connection, which offers a more traditional method for remote access, especially for those not utilizing AWS services. This creates a secure communication layer, allowing devices to connect to the internet and interact with various services.
Before diving in, its often wise to check for firmware updates. Updating the firmware on your IoT device can resolve compatibility issues and improve its overall performance, ensuring your system remains stable and secure.
- Chadwick Boseman Biography Roles Black Panther Legacy
- Randy Watson From Coming To America To Todays News More
In extreme cases, a factory reset might be necessary. However, this should be approached with caution, as it erases all user settings and data. Always back up crucial information before initiating a factory reset, and remember that it could potentially disrupt normal operations.
Remote IoT platforms offer a powerful alternative, allowing users to control devices via a web browser. They can set up a VNC server on a Raspberry Pi and use a VNC client on their device of choice, viewing and interacting with the Pi's desktop from anywhere with an internet connection. The integration of VPNs into remote monitoring further enhances the security by creating an encrypted tunnel for data transmission, safeguarding private information from unauthorized users. Solutions like TeamViewer Tensor offer a flexible and secure approach to remote access, allowing comprehensive management, service, and support from any location, at any time.
RemoteIoT provides a streamlined solution, allowing quick connections to networked Raspberry Pis even when behind a firewall. By following simple steps, RemoteIoT enables secure connection and management of machines and devices from anywhere, including those behind firewalls. All network traffic utilizes an SSH tunnel, providing an extra layer of security.
The RemoteIoT web SSH client offers access from anywhere via a standard web browser. This provides a simple way to connect to your IoT or Raspberry Pi device from your browser. Imagine the convenience of connecting and interacting with your devices, no matter your location, a reality with the right software.
RemoteIoT's device SSH not only ensures secure communication but also simplifies the management of IoT devices remotely. It provides practical insights and actionable tips for effective implementation, offering a secure and efficient way to connect to your Raspberry Pi without complex network configurations. At its core, the RemoteIoT web SSH creates a secure link between your browser and the IoT devices you want to manage.
The first step is registering for an account on the RemoteIoT platform. This opens the door to a 100% open-source IoT device management platform designed for manufacturers and system integrators. Key features include auto-provisioning and white labeling, ensuring scalability, a critical factor for remote IoT monitoring.
IoT devices communicate in various ways, using hundreds of different protocols. In this article, we covered the common elements of an IoT device network, providing examples of how devices send and receive data. IoT devices capture and transfer data within a single network and can be utilized for smart systems, like heat measurement, security systems, smoke detection, and other business or manufacturing needs. Remote IoT device management enables stable equipment performance, predictive maintenance, and damage or danger prevention.
Wired connections, such as those using Ethernet, offer low latency, high reliability, and protection from interference. These are particularly suitable for devices that require a constant and fast connection, such as security systems, surveillance cameras, or industrial monitoring devices.
A robust remote IoT management system should offer specific features, like different scales of device maintenance, reporting capabilities, and troubleshooting tools. Security is also crucial, providing audit logs and user permissions to protect against unauthorized access and data breaches. As deployments grow to include thousands or even millions of devices, it becomes essential to track, monitor, and manage these connected fleets.
Ensuring your IoT devices work properly and securely after deployment is paramount. Secure, exclusive access is pivotal for remote IoT device management and control. Running automated diagnostic scripts can help identify common issues. Being familiar with strategies and knowledge for tackling sudden disruptions helps resolve issues in considerably less time.
Firewalls are a common way to protect and secure access to IoT devices. However, it's challenging to access and manage devices deployed at remote sites, behind firewalls that block all inbound traffic. Troubleshooting often involves sending technicians onsite, increasing complexity and cost. However, solutions like SocketXP allow remote connections to IoT devices behind NAT routers and firewalls from outside networks, such as the internet.
SocketXP is a cloud-based secure remote access solution that allows you to manage and debug embedded Linux devices. Remote IoT device management platforms help monitor and detect uptime, troubleshoot, and address various other problems in your devices. Remote IoT allows you to manage and connect Raspberry Pi or IoT devices securely from anywhere. You can connect to any device or machine behind firewalls.
IoT devices bring automation, efficiency, and convenience. But leaving them unmonitored can create vulnerabilities. In a business setting, remote access is key to maintaining operational continuity, enabling the IT team to resolve issues and provide support without the need for physical presence.
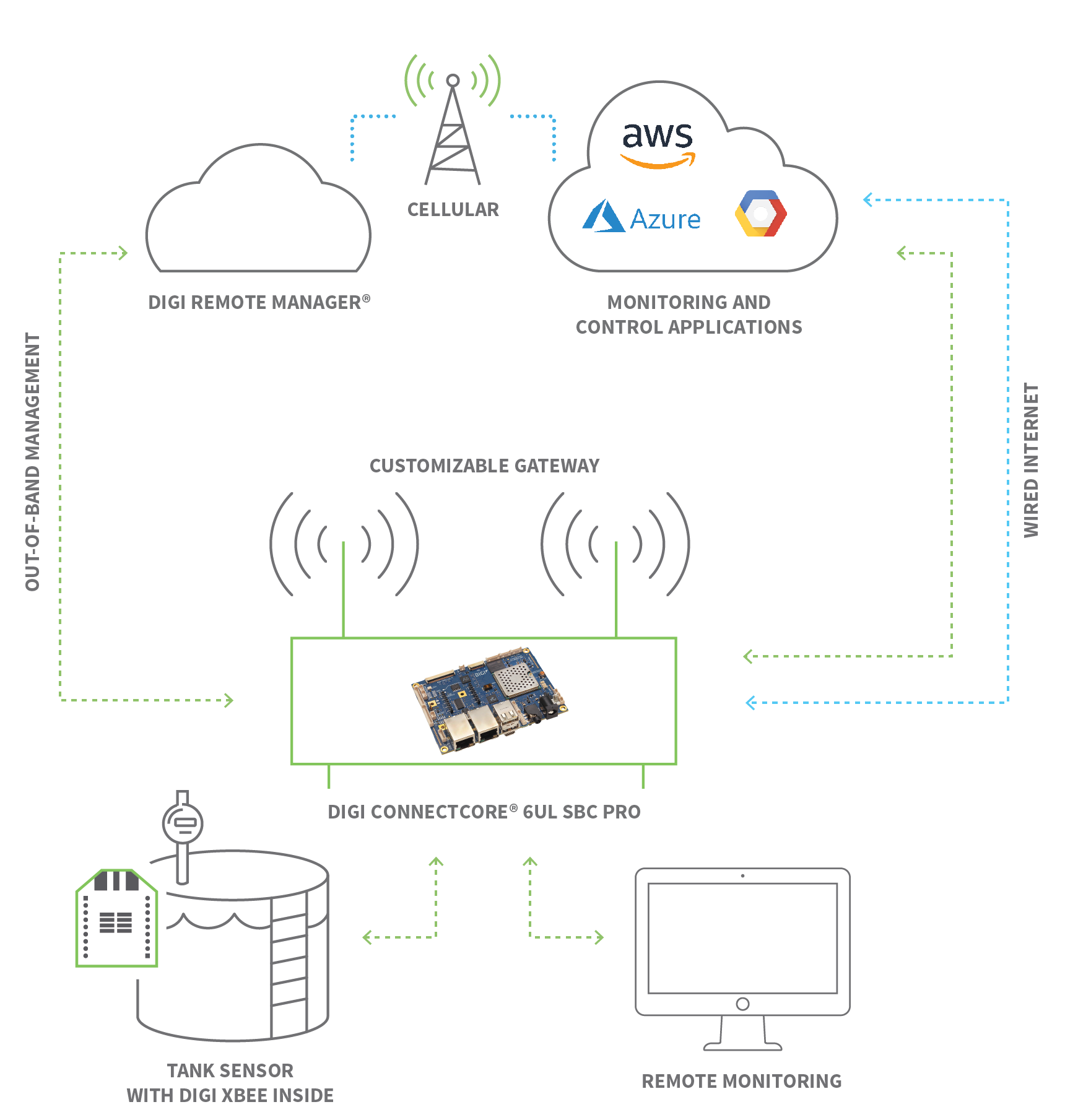
RemoteIoT Device Connect Software Download A Comprehensive Guide
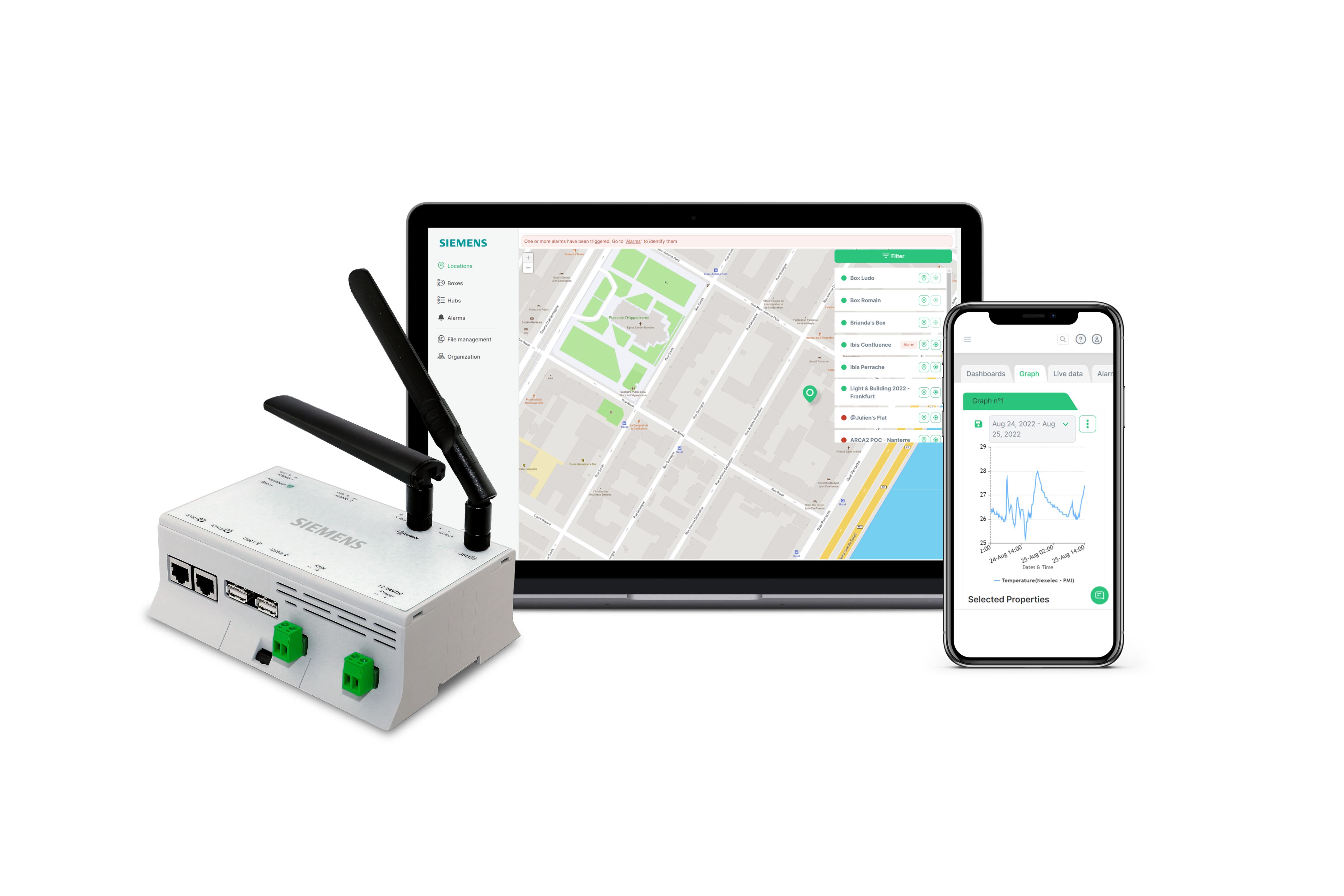
RemoteIoT Device Connect Software Download A Comprehensive Guide

Mastering Secure Connections A Comprehensive Guide To Remotely Connecting IoT Devices Via P2P