Remotely Access IoT Devices Via SSH & Web [Guide]
Are you ready to unlock the full potential of your Internet of Things (IoT) devices from anywhere in the world? Remote access, especially through Secure Shell (SSH), is no longer a luxury but a fundamental requirement for effective IoT device management and maintenance.
The proliferation of IoT devices, from smart home appliances to industrial sensors, has created an unprecedented need for remote management capabilities. Whether you're a hobbyist tinkering with a Raspberry Pi, a system administrator overseeing a fleet of devices, or a service partner needing to troubleshoot equipment in a remote location, the ability to access and control your devices remotely is paramount. Fortunately, a range of solutions have emerged to address this critical need, providing secure and efficient means of accessing your IoT devices, regardless of their location.
One of the most straightforward and widely adopted methods for remote access is SSH (Secure Shell). SSH provides a secure channel for connecting to devices over a network, enabling users to execute commands, transfer files, and manage device configurations as if they were physically present. This secure connection is especially vital in the context of IoT, where devices often handle sensitive data or control critical functions. SSH provides a robust layer of security, protecting devices from unauthorized access and malicious attacks.
- Lori Pettys Relationships Love Life Career Revealed
- Discover Your Free Open Source Iot Device Management Solution
Several platforms and tools have emerged to simplify and enhance the process of remote IoT device access. These solutions cater to different needs and levels of technical expertise. For instance, the remoteiot web SSH client offers a user-friendly interface that allows access to IoT devices through a standard web browser. This eliminates the need for specialized software and provides access from virtually any device with an internet connection. The remoteiot platform even offers a free download option, making it accessible for users seeking to manage their IoT devices remotely without incurring costs.
Beyond SSH, other methods of remote access are available, including VNC (Virtual Network Computing) for graphical remote access. VNC allows users to view and control a device's graphical interface remotely, which is particularly useful for troubleshooting or tasks requiring visual interaction. Furthermore, various cloud-based IoT device management platforms, such as SocketXP, provide comprehensive solutions for remotely managing, accessing, and monitoring IoT devices, Raspberry Pi fleets, or any Linux machines behind a NAT router and firewall.
Let's delve deeper into the advantages and considerations when implementing remote IoT access using SSH and related technologies. We'll look at the different methods, explore security best practices, and examine the challenges and potential solutions for achieving seamless remote access.
- Chadwick Bosemans Wife Life Legacy And What Shes Doing Now
- Ray Charles Life Legacy Soul Music Genius Explore Now
Key Advantages of Using SSH for Remote IoT Access
Utilizing SSH for remote access to IoT devices provides numerous benefits. Here are some of the main advantages:
- Secure Network Service Access: SSH offers a secure tunnel for network service access, even across unprotected networks. This secure connection ensures that sensitive data remains encrypted during transit.
- Remote Management and Monitoring: SSH enables administrators to connect remotely and manage IoT devices without needing to be physically present. Administrators can monitor device performance, troubleshoot issues, and perform software updates from any location with an internet connection.
- Streamlined Management: SSH streamlines the management of IoT devices at scale, leading to improved operational efficiency. This remote management capability is especially valuable for large IoT deployments.
- Reduced Risks: SSH provides a layer of security that helps reduce the risks associated with IoT device management. Secure SSH connections prevent unauthorized access to your devices, protecting sensitive data and system integrity.
How to Get Started with Remote SSH Access
The process of remotely accessing your IoT devices via SSH typically involves the following steps:
- Device Preparation: Ensure that your IoT device, such as a Raspberry Pi, is connected to the internet and has SSH enabled. This may involve configuring the device's network settings and installing an SSH server.
- Install the Remoteiot Agent: Users of the remoteiot platform must download and install the remoteiot agent on their IoT or Raspberry Pi device from the remoteiot portal.
- Network Configuration: Configure your network settings, which might include setting up port forwarding on your router or using a VPN to establish a secure connection.
- SSH Client: Use an SSH client on your computer (Windows, macOS, or Linux) or a web browser (like the remoteiot web SSH client) to connect to your device.
- Authentication: Log in to your device using the required username and password (or SSH keys) when prompted by the SSH client.
- Execution: Once connected, you can execute commands on your device as if you were physically present.
Top Methods to Remotely Access Raspberry Pi and IoT Devices
Several methods can be used to remotely access Raspberry Pi and other IoT devices, including:
- Using SSH for Secure Remote Access: SSH is a widely used and secure way to connect to your devices. It is a dependable method for securely controlling IoT devices.
- Setting Up VNC for Graphical Remote Access: VNC allows you to see and control the graphical interface of your device.
- Cloud-Based IoT Management Platforms: These platforms offer additional functionalities, such as device monitoring, remote access, and security management.
Free Software Options for Remote IoT
Numerous free software options are available for remote IoT access, including:
- SSH Clients: OpenSSH (available on most Linux and macOS systems) and PuTTY (for Windows) are commonly used free SSH clients.
- Remoteiot Web SSH Client: This free client provides an accessible way to connect to your devices through a web browser.
Common Issues and How to Fix Them
When setting up remote access, you may encounter the following common issues:
- Network Connectivity Problems: Ensure your device is connected to the internet and that your network is configured to allow incoming SSH connections.
- Firewall Issues: Firewalls may block incoming SSH connections. Configure your firewall to allow connections on port 22 (the default SSH port).
- Incorrect SSH Configuration: Ensure your SSH server is properly configured with the correct authentication methods (passwords or SSH keys).
- Port Forwarding Problems: If using port forwarding on your router, double-check that the settings are correct and pointing to the correct device's IP address.
- VPN Issues: Ensure the VPN is configured correctly and that it's connected before attempting to SSH into your device.
Security Tips for Remote Access
Security is crucial when setting up remote access. Implement the following security practices:
- Use Strong Passwords or SSH Keys: Use strong, unique passwords or SSH keys to prevent unauthorized access.
- Keep Software Updated: Regularly update your devices and SSH client software to patch security vulnerabilities.
- Disable Password Authentication (Optional): For increased security, disable password authentication and only allow SSH key-based authentication.
- Change the Default SSH Port: Changing the default SSH port (port 22) can help reduce the risk of automated attacks.
- Implement Two-Factor Authentication (2FA): Where possible, enable two-factor authentication for an added layer of security.
Integrating Raspberry Pi with IoT Devices
Raspberry Pi is a popular platform for IoT applications. Integrating a Raspberry Pi with other IoT devices can involve:
- Connecting Sensors and Actuators: Use the GPIO pins on the Raspberry Pi to connect sensors, actuators, and other devices.
- Data Processing and Analysis: Write code (Python or other languages) to process sensor data and make decisions.
- Communication Protocols: Implement communication protocols like MQTT, HTTP, or CoAP to exchange data with other devices and cloud services.
- Remote Access for Control and Monitoring: Use SSH or other remote access methods to monitor and control your Raspberry Pi and its connected IoT devices remotely.
The Role of VPNs in Remote IoT Access
In scenarios where direct SSH access is not feasible or desirable, a VPN (Virtual Private Network) provides an extra layer of security and flexibility. A VPN creates an encrypted tunnel between your device and a remote network, allowing you to connect to your IoT devices as if they were on your local network. With the VPN configured and no VPN connection issues present, connect to your network securely and then access your IoT device through SSH as if you were on your local network. When considering remote access, the use of a VPN can be beneficial.
Service Partners and Remote Access
Service partners often require access to devices installed in remote locations to perform maintenance, troubleshooting, or configuration tasks. Remote access tools like SSH and VNC streamline these tasks, reducing the need for on-site visits and improving efficiency.
Conclusion
The ability to remotely access IoT devices has become an integral part of modern technology management. Secure Shell (SSH) provides a robust method for controlling devices like Raspberry Pis, and a wide range of tools and platforms have been developed to simplify this process, including the remoteiot web SSH client. Whether you're a hobbyist or a service provider, mastering remote access techniques will be essential to managing and maintaining IoT devices effectively.
- Jon Lovitz Age Net Worth Snl Career Everything You Need To Know
- Lilith Berry Real Or Ai Exploring The Mystery Potential
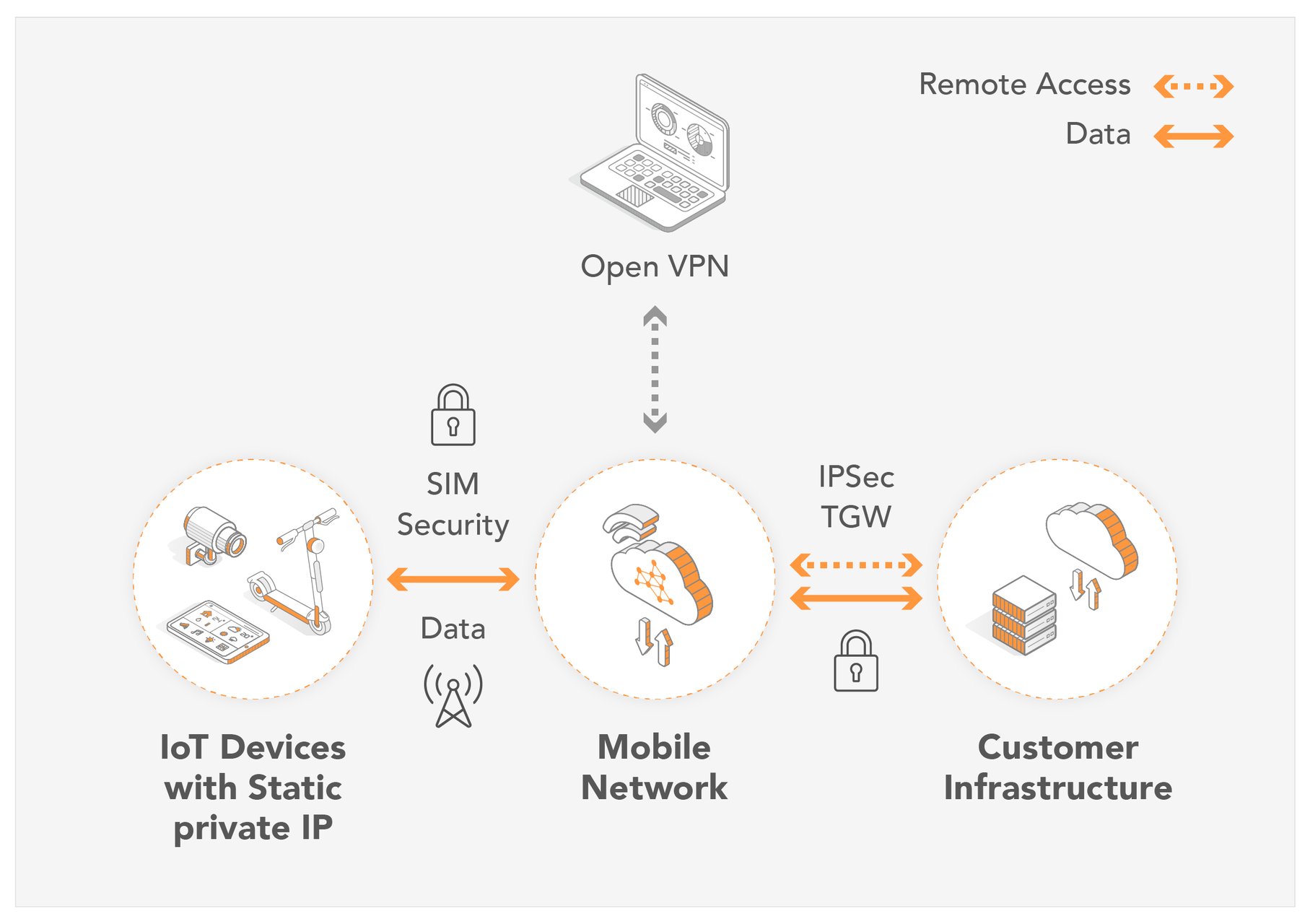
How remote device access helps IoT businesses emnify Blog

Remote Monitoring of IoT Devices Implementations AWS Solutions
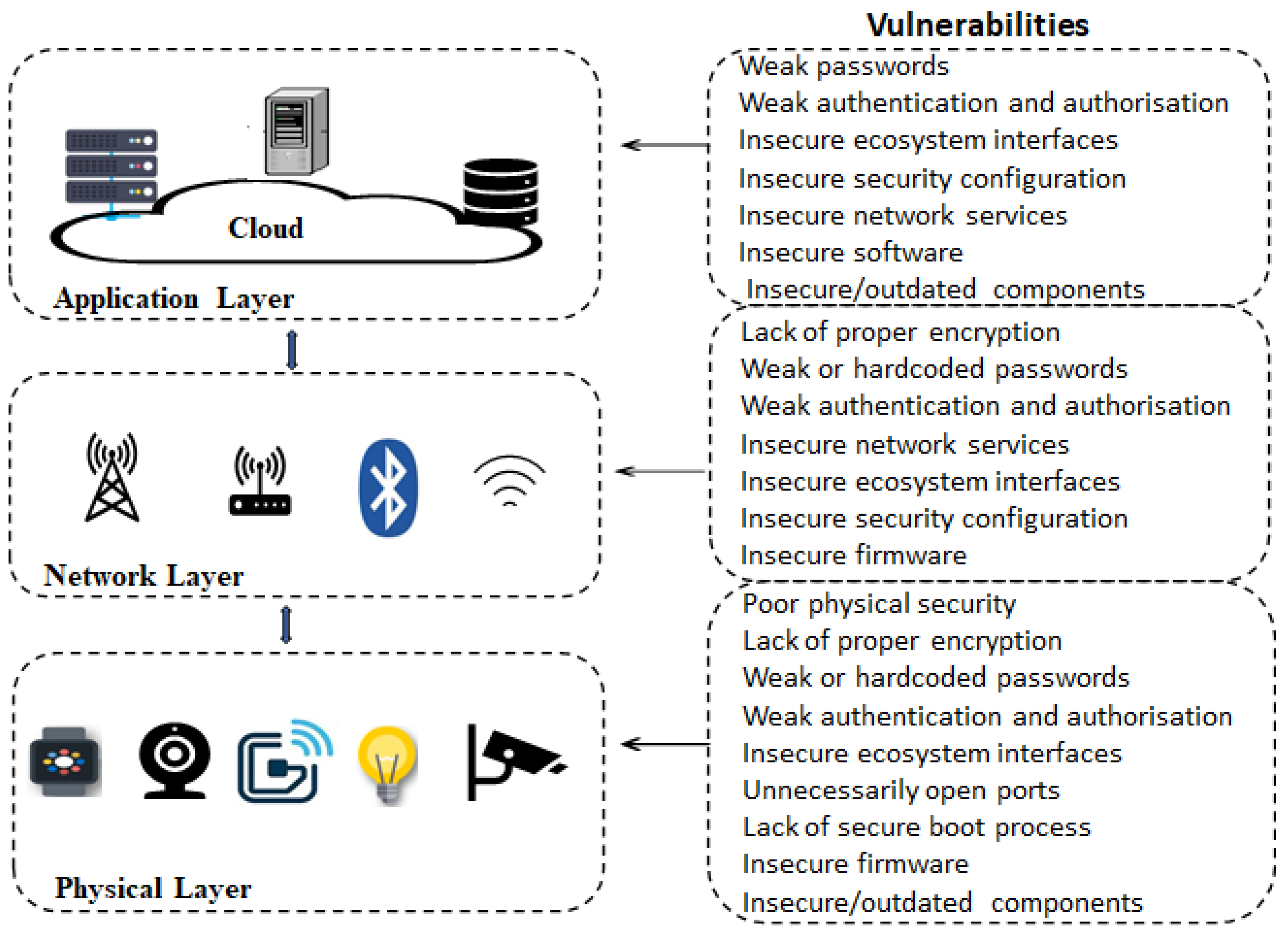
Electronics Free Full Text Analysis of Consumer IoT Device Vulnerability Quantification