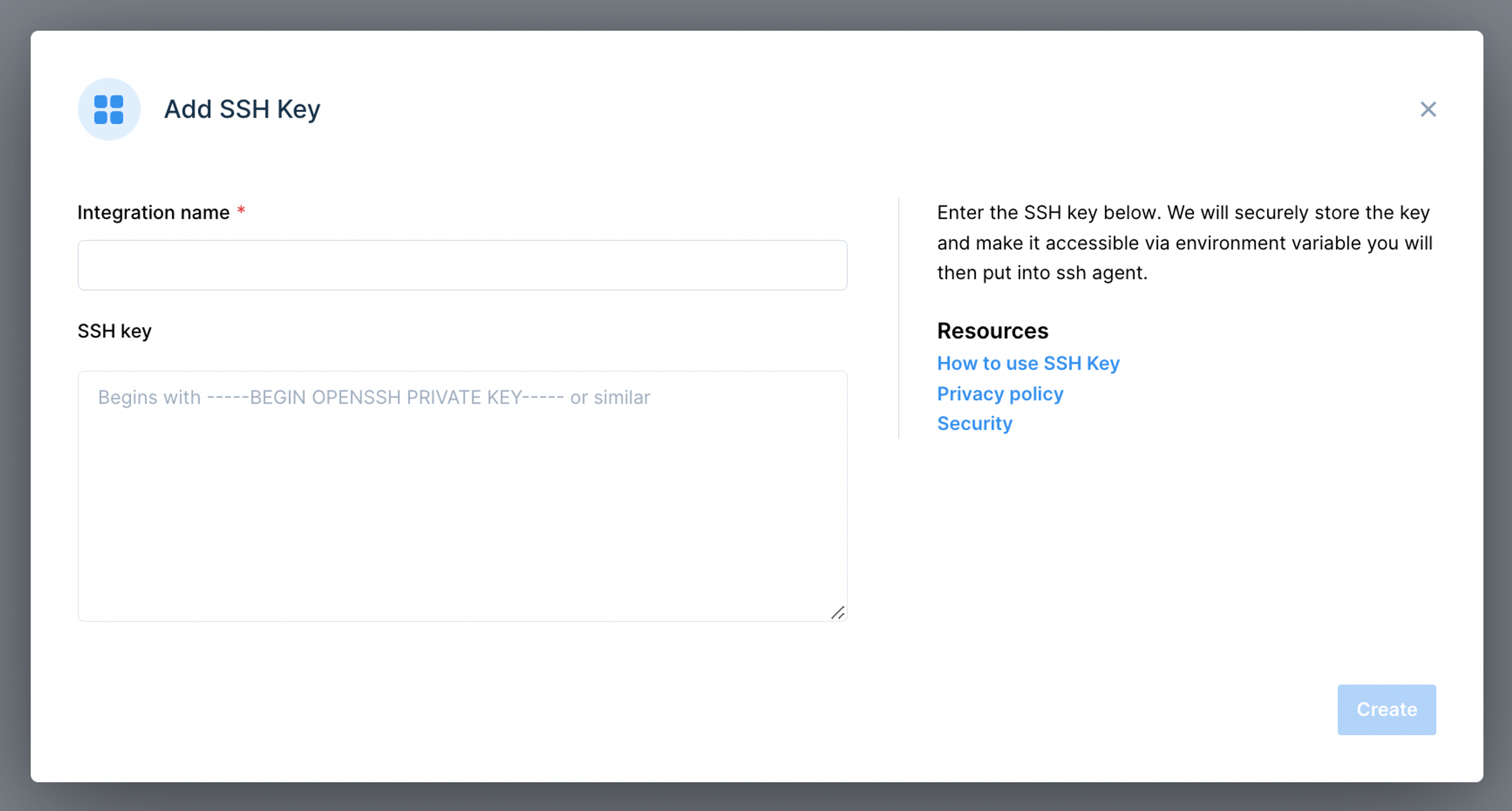
Secure Raspberry Pi IoT: SSH Keys & Remoteiot Platform - Your Guide
Are you tired of juggling complex passwords and struggling with insecure remote access to your Raspberry Pi devices? Embrace the power of SSH keys and the remoteiot platform your gateway to a secure, streamlined, and free IoT experience.
In the ever-evolving landscape of the Internet of Things (IoT), the need for secure and manageable remote access is paramount. Whether you're a seasoned tech professional or a curious hobbyist, the ability to remotely monitor, control, and update your devices is essential. This is where the potent combination of Secure Shell (SSH) keys and platforms like remoteiot steps in, offering a robust solution to safeguard your data and simplify your workflow.
One of the critical components of this setup is Secure Shell (SSH), which allows secure communication between devices.
- Francis Escudero Net Worth 2024 How Rich Is The Politician
- Laro Benz Ethnicity Family Amp Career Unveiling His Story
The beauty of this setup lies in its simplicity. You can use the remoteiot secure IoT cloud platform to quickly connect to networked Raspberry Pi from anywhere, even if it's behind a firewall. Just follow these 3 simple steps.
This guide delves into how the remoteiot platform simplifies SSH key management for Raspberry Pi, ensuring your devices remain secure and accessible. We'll explore the fundamentals of SSH keys, the benefits of utilizing a remote IoT platform, and a step-by-step approach to configuring this powerful combination.
The integration of SSH keys with Raspberry Pi through the remoteiot platform not only enhances security but also simplifies device management. Platforms enhance convenience, security, and scalability, making them an attractive option for both personal and professional projects.
- Miaz Girthmaster Unveiling The Viral Sensations World
- Randy Watson From Coming To America To Todays News More
When you set up an SSH key in the remoteiot platform, you're essentially creating a secure channel for communication. First, you generate a key pair on your system.
Remoteiot platforms are designed to simplify the management of IoT devices, providing users with the ability to monitor and control devices remotely.
Imagine this—you're sitting in your favorite coffee shop, sipping on a warm latte, and suddenly you realize you need to check your IoT devices back at home. By leveraging SSH keys, administrators can securely manage devices from anywhere in the world.
The remoteiot platform leverages SSH keys to secure communication between IoT devices and the central server. When a new device is added to the platform, it generates an SSH key pair. The public key is uploaded to the server, while the private key is stored securely on the device.
The remoteiot platform is a powerful tool designed to manage and monitor IoT devices remotely. The remoteiot platforms SSH key feature for Raspberry Pi is free of charge.
Setting up SSH keys instead of passwords is an even stronger move. By keeping an eye on these trends, you can ensure that your free remote IoT platform remains relevant and competitive in the years to come.
By following the steps outlined in this article, you can enhance the security and usability of your IoT infrastructure. Many Raspberry Pi users face similar challenges when setting up Secure Shell (SSH) connections for remote access. The remoteiot platform is like the swiss army knife for managing IoT devices, including your trusty Raspberry Pi. It lets developers control, monitor, and update devices from one central place.
In this article, well explore how the remoteiot platform simplifies SSH key management for Raspberry Pi, ensuring your devices remain secure and accessible. Whether you're setting up a smart home, building an IoT project, or managing remote servers, SSH keys are your golden ticket to secure, seamless access.
Heres a simple breakdown to get you started on how to set this up, which is one of the key advantages of using a remote IoT platform.
If you're diving into the world of IoT (Internet of Things) and exploring the remoteiot platform, then you're in the right place. In this guide, Ill walk you through everything you need to know about configuring SSH keys for Raspberry Pi using the remoteiot platform.
The remoteiot platform SSH key free solution is here to revolutionize your workflow. This innovative platform allows users to access and manage IoT devices with ease, eliminating the need for cumbersome SSH keys.
Ssh is secure, but people should still take some basic precautions.
Remoteiot supports centralized management of
In conclusion, setting up a free remote IoT platform using SSH keys and a Raspberry Pi is a fantastic way to explore the world of IoT without breaking the bank. Are you struggling with the remoteiot platform SSH key not working on your Raspberry Pi? If yes, youre not alone.
Alright, lets start with the basics. The remoteiot platform is like the swiss army knife for managing IoT devices, including your trusty Raspberry Pi. It lets developers control, monitor, and update devices from one central place.
Whether you're a hobbyist looking to automate your home or a business owner seeking to optimize your operations, this setup offers endless possibilities. In conclusion, the remoteiot platform provides a powerful solution for managing IoT devices, particularly when paired with Raspberry Pi and secure SSH key configurations. The public key is uploaded to the server, while the private key is stored securely on the device.
Here's a detailed look at the core components:
SSH Keys: The Foundation of Secure Remote Access
SSH keys are cryptographic keys that provide a more secure way to authenticate to a device than using passwords. Instead of typing in a password every time you want to connect, you use a key pair: a public key and a private key. The public key is placed on the device you want to access, and the private key is kept secret on your local machine. When you connect, the server verifies your identity by checking if the key you presented is associated with the public key it has on file.
The Benefits of SSH Keys
- Enhanced Security: SSH keys are significantly more secure than passwords. They are less susceptible to brute-force attacks and other common hacking methods.
- Convenience: Once set up, SSH keys eliminate the need to repeatedly type in passwords, making remote access much more convenient.
- Automation: SSH keys can be used in scripts and automated processes, allowing you to manage your devices without manual intervention.
- Compliance: Many security standards and best practices recommend the use of SSH keys over passwords for remote access.
The RemoteIoT Platform: Your Centralized Hub
The remoteiot platform serves as a central point for managing your IoT devices. It streamlines the process of managing SSH keys, making it easier than ever to secure your devices. RemoteIoT simplifies SSH key management for Raspberry Pi by automating the generation, deployment, and management of SSH keys, reducing manual effort and minimizing errors. Its intuitive interface makes it accessible for users of all skill levels.
Key features of the RemoteIoT Platform include:
- Centralized Key Management: Easily generate, store, and manage SSH keys for all your devices in one place.
- Automated Deployment: Automatically deploy the public key to your Raspberry Pi devices, saving you time and effort.
- Remote Access: Securely connect to your devices from anywhere with an internet connection.
- Monitoring and Alerting: Monitor the status of your devices and receive alerts if there are any issues.
Step-by-Step Guide to Configuring SSH Keys with Raspberry Pi and RemoteIoT
The specific steps may vary slightly depending on the remoteiot platform and your exact setup, but the general process involves the following:
- Account Setup: Create an account on the remoteiot platform if you don't already have one.
- Device Registration: Add your Raspberry Pi to the remoteiot platform. This usually involves installing a small agent on your Raspberry Pi and linking it to your account.
- Key Generation: The remoteiot platform may automatically generate SSH key pairs for each of your devices or provide instructions for generating them yourself.
- Key Deployment: The platform will then deploy the public key to your Raspberry Pi.
- Connecting: You can then use an SSH client (like PuTTY or the built-in SSH client on Linux and macOS) to connect to your Raspberry Pi using your private key.
Troubleshooting Common Issues
- Key Permissions: Make sure that the private key has the correct permissions (typically read-only for the user).
- Firewall Rules: Ensure that your Raspberry Pi's firewall is configured to allow SSH connections on port 22 (or your custom port).
- Incorrect Key Path: Double-check that you are providing the correct path to your private key in your SSH client.
- Platform-Specific Documentation: Consult the remoteiot platform's documentation for specific troubleshooting steps.
Embracing the Future of IoT Security
The combination of SSH keys and a platform like remoteiot is a powerful way to secure and manage your IoT devices. SSH is secure, but people should still take some basic precautions. Setting up SSH keys instead of passwords is an even stronger move. As IoT technology continues to evolve, prioritizing security and simplifying device management will be more important than ever.
By following the steps outlined in this guide, you can confidently set up a secure, remote access for your Raspberry Pi and IoT devices, opening up a world of possibilities for your projects.
Remember, the remoteiot platform SSH key free solution is here to revolutionize your workflow. This innovative platform allows users to access and manage IoT devices with ease, eliminating the need for cumbersome SSH keys.
Remote IoT platforms offer numerous advantages, from increased efficiency to enhanced security.
This section will outline the key benefits of using a remote IoT platform, focusing on how SSH keys contribute to a more secure and streamlined environment.
Here's a table summarizing the core advantages and the role SSH keys play:
| Benefit | How SSH Keys Contribute |
|---|---|
| Enhanced Security: Reduced risk of unauthorized access. |
|
| Simplified Device Management: Easier control and monitoring of devices. |
|
| Increased Efficiency: Saves time and resources. |
|
| Improved Scalability: Easily manage a growing number of devices. |
|
| Enhanced Compliance: Meets security best practices. |
|
The remoteiot platform provides a powerful solution for managing IoT devices, particularly when paired with Raspberry Pi and secure SSH key configurations.
Ssh your IoT device with the system user or SSH key-based secure authentication and these standard client tools such as PuTTY.
- Unveiling The Truth The Anna Malygon Onlyfans Leak Its Impact
- Cynthia Erivo The Greatest Showman A Look Beyond The Stage
RemoteIoT Platform SSH Key Free Android The Ultimate Guide For Secure Connectivity

Mastering RemoteIoT Platform SSH Key Raspberry Pi Setup A Comprehensive Guide
RemoteIoT Platform SSH Key Free Android The Ultimate Guide For Secure Connectivity