Secure Remote IoT Access: Your Guide To Remoteiot & SSH
Ever wondered how to effortlessly manage your Internet of Things (IoT) devices from anywhere, anytime, and with unparalleled security? The answer lies in the power of remote access solutions, specifically leveraging the robust capabilities of Secure Shell (SSH) and platforms like RemoteIoT. This sophisticated technology not only simplifies device management but also fortifies your digital infrastructure against potential threats.
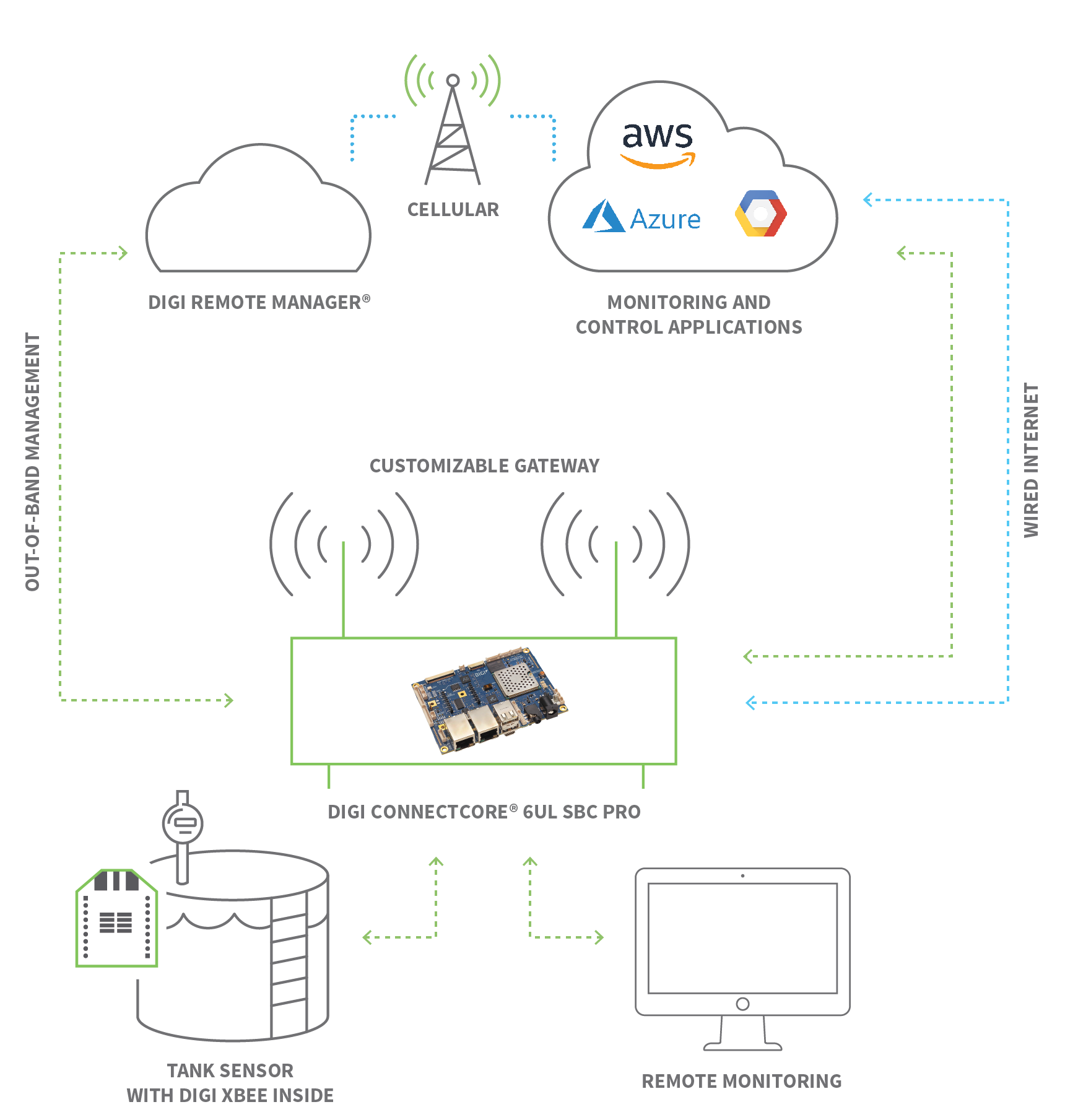
The beauty of these solutions is their versatility. You can connect to devices, even those tucked behind the protective walls of firewalls, ensuring that geographical limitations don't restrict your control. All network traffic is meticulously encrypted through an SSH tunnel, a secure passageway that shields your data from prying eyes. Not even the RemoteIoT platform itself can decipher the information flowing within these tunnels, guaranteeing a level of privacy that is paramount in today's interconnected world.
Embarking on this journey requires a few simple steps. Begin by opening the terminal on your Raspberry Pi, or access it remotely via SSH on your local network. From there, install the RemoteIoT service. Next, navigate to the RemoteIoT portal in your preferred web browser and log in to your dashboard. You should find your Raspberry Pi listed amongst your account devices, ready for remote management. This initial setup is your gateway to a world of streamlined control and enhanced security.
- Lilith Berry Real Or Ai Exploring The Mystery Potential
- Charlie Hurts Salary Net Worth What You Need To Know
So, what exactly is the allure of SSH in the context of RemoteIoT? SSH, or Secure Shell, is fundamentally a cryptographic network protocol. Its primary function is to facilitate secure connections to remote systems over a network. When we speak of SSH within the RemoteIoT framework, we're essentially utilizing this protocol to remotely access and control IoT devices, such as your dependable Raspberry Pi. This allows for a secure, encrypted channel for communication and control, protecting sensitive data from interception or tampering.
To establish a connection to your IoT device, you'll typically need to execute a specific command. This command varies depending on your chosen platform, but the core principle remains consistent. When prompted, carefully enter the required credentials your username and password to authenticate your access. These steps are crucial for verifying your identity and ensuring that only authorized users can interact with your devices.
With these fundamental procedures completed, you will successfully establish a secure RemoteIoT VPC SSH connection, even on a Windows 10 system. This connection acts as a digital bridge, granting you remote access to your devices while ensuring data confidentiality. These steps pave the way for robust, secure management of IoT devices.
- Seo Ji Hye Dating Life Marriage Views Career What You Need To Know
- Lori Pettys Relationships Love Life Career Revealed
The importance of security in remote IoT device management cannot be overstated. Security should be at the forefront of your mind when dealing with IoT devices remotely. Any vulnerability can expose your devices and, potentially, your entire network, to a range of cyber threats. Robust security protocols and diligent implementation are indispensable to a secure setup.
After you install RemoteIoT, the next phase involves configuring your Raspberry Pi to work harmoniously with the platform. This process involves several key steps, beginning with running a specific command designed to connect your device to your RemoteIoT account. You will be prompted to enter your account credentials, confirming your identity and granting you access to manage your device.
Once authenticated, your Raspberry Pi will make its appearance within the RemoteIoT dashboard. Here, you will have a consolidated view of your devices, allowing you to monitor their status, manage settings, and issue commands from a centralized location. This dashboard interface streamlines your device management process, making it easier than ever to keep track of your IoT ecosystem.
Following a successful connection, the RemoteIoT CLI (Command Line Interface) can be installed on your Raspberry Pi. The CLI provides the tools needed to establish and maintain a secure connection to your VPC (Virtual Private Cloud). This process can involve the configuration of network settings, fine-tuning firewall rules, and ensuring that your device is accessible over the internet.
Understanding remote IoT device management is not just a technical exercise, its an investment in the security and future growth of your business. Knowledge empowers you to make informed decisions about your network infrastructure and helps your business by fostering secure and efficient operations. This knowledge also extends to understanding how to choose IoT consulting services that align with your specific needs and goals.
Several options for remote access solutions make it easy to manage devices over the Internet. These solutions offer flexibility, enabling remote management over the internet. The common options include:
- Remotely connect to IoT devices behind NAT routers or firewalls using SSH: SSH is the cornerstone of secure remote access. It allows you to create encrypted tunnels that bypass firewalls and NAT routers, granting you secure access.
- Connect to IoT devices remotely over the internet using VNC: Virtual Network Computing (VNC) offers a graphical remote access solution, enabling you to see and control the screen of your IoT device as if you were sitting in front of it.
- Connect to IoT Remote Desktop (RDP) over the internet using XRDP: XRDP enables remote desktop connections. This is particularly useful for accessing the graphical user interface (GUI) of your IoT device, offering a user-friendly access method.
- Remote control IoT devices behind a NAT router or firewall using a web app: Web-based applications provide a user-friendly interface for managing and controlling IoT devices. They offer the flexibility to be accessed from any device with a web browser.
- Send remote commands to IoT devices over the internet from outside: This functionality empowers you to execute commands on your IoT devices remotely. This allows you to control aspects like data collection, software updates, and settings adjustments.
When establishing a remote desktop connection, selecting the right method is important. For example, connecting remotely using the SocketXP IoT device remote access solution requires entering the IP address (typically localhost or 127.0.0.1) and the port number (e.g., 3000) in the RDC (Remote Desktop Connection) client. This configuration creates a direct link between your local system and the IoT device.
Creating a secure remote connection for your Raspberry Pi, using a VPC to an AWS server, emphasizes the importance of establishing a stable and secure connection. This ensures data is protected while giving you access to your IoT devices, regardless of your location. Its similar to building a secure, digital fortress to safeguard your gadgets, where only the right keys can unlock the gates.
SSH (Secure Shell) is a cryptographic network protocol. Its role is to securely access remote systems. It ensures that communication is encrypted and protected from potential security threats. This security is essential for remote device management, where unauthorized access could lead to data breaches or system compromise.
AWS IoT device management allows you to secure and manage IoT devices at scale. The platform allows you to manage the lifecycle of your devices, including onboarding, organizing, monitoring, and managing them remotely. This approach allows for the efficient management of large fleets of devices.
When you start, you can follow these simple steps to securely connect your remote IoT devices using p2p SSH on Windows for free. This is an accessible option for users who want to test the capabilities of secure remote access.
By understanding these methods and the security measures they employ, you can create a more robust and reliable IoT ecosystem. These methods guarantee that your devices are always accessible and secure, no matter where you are.
- Jason Kylie Kelce Welcome Baby Finnley See The Sweet Details
- Lori Pettys Relationships Love Life Career Revealed
RemoteIoT Device Connect Software Download A Comprehensive Guide

IoT Remote Desktop Anyway Navigating Remote Work With IoT

Connecting IoT Devices Securely With Raspberry Pi A Beginner's Guide