Master IoT Security: Controlling Devices Behind A Firewall
Are you grappling with the complexities of securing your Internet of Things (IoT) devices? In today's digital landscape, safeguarding your IoT network is paramount, and mastering the art of controlling these devices behind a firewall is no longer optional; it's essential.
The proliferation of IoT devices, from smart home appliances to industrial sensors, has created unprecedented opportunities for innovation and efficiency. However, this expansion has also widened the attack surface for cyber threats. An IoT firewall emerges as a vital security system, designed to protect these devices and the networks they inhabit from a myriad of online dangers. Its primary objective is to prevent unauthorized access, acting as a vigilant gatekeeper that scrutinizes all incoming and outgoing traffic.
The crucial role of a firewall in the IoT ecosystem cannot be overstated. By acting as a protective barrier, it ensures that only authorized traffic can traverse the network, effectively shielding your devices from potential threats. This proactive approach is crucial for maintaining the integrity and confidentiality of your data, while also ensuring the smooth operation of your interconnected devices. Consider a modern, innovative home environment, where remote access to appliances becomes a necessity. You might need to adjust the settings of your smart oven or monitor your security system even when you are not physically present. This remote control is often facilitated through a network, and a robust firewall is key to maintaining this level of convenience while maintaining security.
- Secure Remote Access Your Guide To Remoteiot Alternatives
- Jon Lovitz Age Net Worth Snl Career Everything You Need To Know
Remote access and control of IoT devices behind a firewall is also crucial for managing IoT networks efficiently and ensuring they operate without interruption. From the perspective of remote maintenance and troubleshooting to deploying updates, the ability to securely connect to devices behind a firewall allows for immediate action to maintain optimal performance.
Fortunately, several methods and technologies are available to help you control your IoT devices securely and efficiently, without compromising your network's integrity. These methods range from leveraging cloud services like AWS to employing more direct techniques. When utilizing a web application for remote access, installing and running a web application on your IoT device can allow for secure remote access using a web client.
When considering controlling your IoT devices, picking the suitable firewall option for your business needs is critical. The best approach will depend on your IoT devices and their internal network configuration. IoT network firewalls or converting existing devices to include inbuilt firewalls are two potential solutions. The selection depends entirely on your environment and your need to secure your network.
- Sean Paul Lockhart Brent Corrigan Movies Bio More
- Fix Raspberry Pi Vnc Viewer On Windows 10 Free Solutions Tips
Managing your Raspberry Pi behind a firewall or a NAT router without a public IP address presents a significant challenge for remote control and maintenance. This can be circumvented with solutions such as directly connecting to your Raspberry Pi from anywhere as if it was on your local network, and sending commands and batch jobs from web portals. Changing VPN or firewall configuration can be challenging, particularly if the Raspberry Pi is behind a corporate firewall that does not allow SSH or VNC connections.
The use of IoT remote control behind a firewall is also expanding rapidly, especially with the proliferation of devices using Android. These solutions are essential for businesses and individuals alike. As the world becomes increasingly interconnected, these solutions will continue to evolve.
For IT professionals and tech enthusiasts alike, knowing how to control IoT devices behind a firewall, especially on Ubuntu, has become an important skill.
To summarize, an IoT firewall acts as a first line of defense, examining the traffic from your devices and only permitting authorized data to pass. It is also essential for managing the security of your network and protecting it from a number of cyber threats. Furthermore, remote access and control are extremely beneficial for keeping your IoT networks running efficiently. If you're looking for ideas on how to remotely control your devices, read our guide about remote control for iPads.
There are several methods available to remotely access and control your IoT devices. One such method involves installing and running a web application on your IoT device, which enables remote connections via a web client. Another approach is to use cloud services such as AWS, which allows you to control IoT devices behind a firewall. This necessitates establishing a secure communication channel between the device and the cloud.
To further break down the essential components, here is a structured overview of the crucial aspects of managing IoT devices behind a firewall. This serves as a foundational guideline, setting the stage for a more detailed analysis of tools, best practices, and future trends:
| Aspect | Description |
|---|---|
| Firewall Role | Acts as a protective barrier between IoT devices and the external network (internet or local networks). |
| Traffic Control | Monitors and controls both incoming and outgoing traffic to and from IoT devices. |
| Security | Offers an extra layer of security to safeguard IoT devices from online threats. |
| Remote Access | Enables remote management of IoT devices, which is crucial for efficient operation and maintenance. |
| Key Technologies | AWS and other methods for establishing secure communication channels. Web apps for remote access. |
| Software and Tools | Lightweight messaging protocols, setting up environments such as Ubuntu, and firewall configuration tools are often used. |
Numerous tools and software solutions are available to facilitate the control of IoT devices behind firewalls. These resources range from lightweight messaging protocols, which are ideal for IoT communication, to dedicated platforms for remote management. You can use software on Ubuntu to manage your IoT devices. This can provide further control over your network.
The implementation of secure protocols and practices is crucial. These considerations include: setting up a secure Ubuntu environment, configuring firewalls correctly, and continuously monitoring the network for potential threats. When creating your network, always consider the most appropriate methods of management.
The ability to manage IoT devices behind a firewall is essential for protecting networks from cyber threats. As the number of connected devices grows, so does the significance of ensuring secure communication. Selecting an appropriate firewall and implementing the best practices for security and management are key steps in the development of a safe IoT environment.
Controlling IoT devices behind a firewall has become essential for businesses and individuals alike. This is because the Internet of Things (IoT) is expanding exponentially. Controlling IoT devices behind a firewall is a critical aspect of cybersecurity.
As the IoT landscape continues to expand, staying informed about the latest trends in IoT and firewall technology is crucial. The integration of AI-powered firewalls and the adoption of zero-trust architectures are just a few of the developments that are shaping the future of IoT security. Furthermore, always consider which firewall option best meets the needs of your business. IoT network firewalls or even converting IoT devices to include built-in firewalls can be considered. All of these possibilities can enhance the security and control of your network.
In the interconnected world, controlling IoT devices behind a firewall is a critical skill for IT professionals and tech enthusiasts alike. This approach enhances the security and management of IoT devices. Moreover, as more devices become connected, the need to ensure secure communication between these devices and networks is becoming increasingly important.
Remember to continuously learn and apply this knowledge to create a safe and secure IoT ecosystem for the present and the future. As you implement these strategies, you will be able to control your IoT devices, protect your network, and optimize your device management strategies.
- Charlie Hurts Salary Net Worth What You Need To Know
- Randy Watson From Coming To America To Todays News More

Mastering Remote IoT Connectivity A Comprehensive Guide To Accessing IoT Devices Behind

How To Use RemoteIoT Behind Firewall Windows A Comprehensive Guide
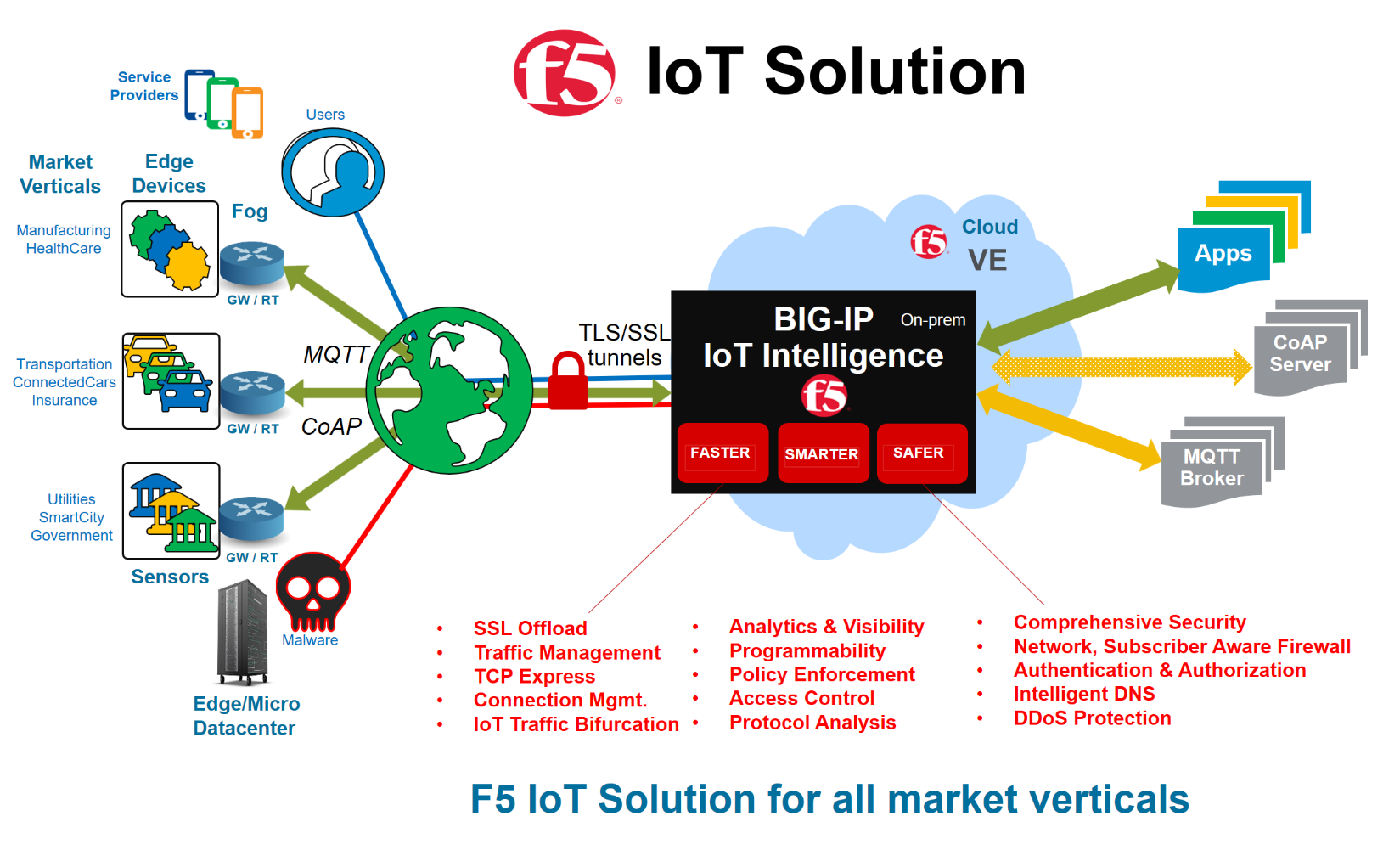
IoT Infrastructure, Empowered by F5’s IoT Solution